Log On-Off 내역 분석
RDP Connection 내역
아래 명령을 실행하면 환경변수 $TEMP로 설정된 디렉토리에 csv 파일이 저장된다.
F:\script\powershell>powershell -executionpolicy bypass -f RDPConnectionParser.ps1
Writing File: f:\Temp\2020-03-03T16.24.38_RDP_Report.csv
Done!
F:\script\powershell>type f:\temp\2020-03-03T16.24.38_RDP_Report.csv
"TimeCreated","User","ServerName","IPAddress","EventID","Action"
"2020-02-17 ?? 12:45:59","CHOHB\chohb","chohb","LOCAL","21","logon"
"2020-02-17 ?? 6:02:33","CHOHB\chohb","chohb",,"23","logoff"
"2020-02-18 ?? 8:47:25","CHOHB\chohb","chohb","LOCAL","21","logon"
"2020-02-18 ?? 6:02:18","CHOHB\chohb","chohb",,"23","logoff"
< 참고 >
Event ID가 21이면 RDP logon,
Event ID가 22이면 RDP Shell Start,
Event ID가 23이면 RDP logoff,
Event ID가 24이면 RDP DisConnected,
Event ID가 25이면 RDP ReConnection
이벤트 로그 조회
Session 관련 이벤트 파일
F:\temp>dir %windir%\system32\winevt\logs\*session*.evtx
Microsoft-Windows-RemoteDesktopServices-SessionServices%4Operational.evtx
Microsoft-Windows-TerminalServices-LocalSessionManager%4Admin.evtx
Microsoft-Windows-TerminalServices-LocalSessionManager%4Operational.evtx
< RDP Files >
%User Profile%\Documents\Default.rdp 파일도 일단 수집하자.
분석 대상 시스템에서 RDP 접속을 한 흔적 파악하는데 사용될 수 있다. RDP 접속 후 네트워크를 통해 용의자가 파일을 전송하였거나, 정보를 획득할 수 있다는 가능성을 제기할 수 있으며, 침해사고 관점에서는 원치 않은 접속 요청에 대한 정보를 수집하여 시스템의 악성 행위 시점을 판단하는데 도움을 줄 수 있다.
파일 저장
F:\temp>wevtutil epl /lf "C:\WINDOWS\system32\winevt\logs\Microsoft-Windows-TerminalServices-LocalSessionManager%4Operational.evtx" "c:\temp\TerminalServices-LocalSessionManager-Operational.evtx"
컬럼명 조회
C:\>LogParser.exe -h -i:evt "c:\temp\TerminalServices-LocalSessionManager-Operational.evtx"
조회
F:\temp>LogParser.exe -stats:off -i:evt "select Timegenerated, strings, Eventid from 'c:\temp\TerminalServices-LocalSessionManager-Operational.evtx' where Eventid='21' or Eventid='22' or Eventid='23' or Eventid='24' or Eventid='25'"
C:\DFIR\EventLog>wevtutil epl system system-export.evtx
Security 이벤트 파일
C:\DFIR\EventLog>wevtutil epl security security-export.evtx
C:\>LogParser.exe -stats:OFF -i:EVT "SELECT TimeGenerated AS Date, EXTRACT_TOKEN(Strings, 5, '|') as Username, EXTRACT_TOKEN(Strings, 6, '|') as Domain, EXTRACT_TOKEN(Strings, 8, '|') as LogonType,EXTRACT_TOKEN(strings, 9, '|') AS AuthPackage, EXTRACT_TOKEN(Strings, 11, '|') AS Workstation, EXTRACT_TOKEN(Strings, 17, '|') AS ProcessName, EXTRACT_TOKEN(Strings, 18, '|') AS SourceIP FROM 'C:\temp\Security-Export.evtx' WHERE EventID = 4624 AND Username NOT IN ('SYSTEM'; 'ANONYMOUS LOGON'; 'LOCAL SERVICE'; 'NETWORK SERVICE') AND Domain NOT IN ('NT AUTHORITY') and EXTRACT_TOKEN(Strings, 8, '|')='10' "
< 참고 > 이벤트 로그 내용을 Text로 저장
C:\>wevtutil qe /lf "C:\WINDOWS\system32\winevt\logs\Microsoft-Windows-TerminalServices-LocalSessionManager%4Operational.evtx" /f:text > "c:\temp\TerminalServices-LocalSessionManager-Operational.txt"
System 이벤트 파일
C:\DFIR\EventLog>wevtutil epl system system-export.evtx
동일한 방법으로 조회
NTLM Based Logon
possible pass-the-hash
C:\>LogParser.exe -stats:OFF -i:EVT "SELECT TimeGenerated AS Date, EXTRACT_TOKEN(Strings, 5, '|') as Username, EXTRACT_TOKEN(Strings, 6, '|') as Domain, EXTRACT_TOKEN(Strings, 8, '|') as LogonType, EXTRACT_TOKEN(strings, 10, '|') AS AuthPackage, EXTRACT_TOKEN(Strings, 11, '|') AS Workstation, EXTRACT_TOKEN(Strings, 17, '|') AS ProcessName, EXTRACT_TOKEN(Strings, 18, '|') AS SourceIP FROM 'C:\temp\Security-Export.evtx' WHERE EventID = 4624 AND Username NOT IN ('SYSTEM'; 'ANONYMOUS LOGON'; 'LOCAL SERVICE'; 'NETWORK SERVICE') AND Domain NOT IN ('NT AUTHORITY') AND AuthPackage LIKE '%NtLmSsp%' AND Username NOT LIKE '%$'"
All Logon History
이벤트 ID 4624에 대한 로그인 유형

로그인 유형에 대해 각각 조회가 가능하다.
C:\>LogParser.exe -stats:OFF -i:EVT "SELECT TimeGenerated AS Date, EXTRACT_TOKEN(Strings, 5, '|') as Username, EXTRACT_TOKEN(Strings, 6, '|') as Domain, EXTRACT_TOKEN(Strings, 8, '|') as LogonType,EXTRACT_TOKEN(strings, 9, '|') AS AuthPackage, EXTRACT_TOKEN(Strings, 11, '|') AS Workstation, EXTRACT_TOKEN(Strings, 17, '|') AS ProcessName, EXTRACT_TOKEN(Strings, 18, '|') AS SourceIP FROM 'C:\temp\Security-Export.evtx' WHERE EventID = 4624 AND Username NOT IN ('SYSTEM'; 'ANONYMOUS LOGON'; 'LOCAL SERVICE'; 'NETWORK SERVICE') AND Domain NOT IN ('NT AUTHORITY')"
콘솔 로그인
C:\>LogParser.exe -stats:OFF -i:EVT "SELECT TimeGenerated AS Date, EXTRACT_TOKEN(Strings, 5, '|') as Username, EXTRACT_TOKEN(Strings, 6, '|') as Domain, EXTRACT_TOKEN(Strings, 8, '|') as LogonType,EXTRACT_TOKEN(strings, 9, '|') AS AuthPackage, EXTRACT_TOKEN(Strings, 11, '|') AS Workstation, EXTRACT_TOKEN(Strings, 17, '|') AS ProcessName, EXTRACT_TOKEN(Strings, 18, '|') AS SourceIP FROM 'C:\temp\Security-Export.evtx' WHERE EventID = 4624 AND Username NOT IN ('SYSTEM'; 'ANONYMOUS LOGON'; 'LOCAL SERVICE'; 'NETWORK SERVICE') AND Domain NOT IN ('NT AUTHORITY') and EXTRACT_TOKEN(Strings, 8, '|')='2' "
네트워크 로그인
C:\>LogParser.exe -stats:OFF -i:EVT "SELECT TimeGenerated AS Date, EXTRACT_TOKEN(Strings, 5, '|') as Username, EXTRACT_TOKEN(Strings, 6, '|') as Domain, EXTRACT_TOKEN(Strings, 8, '|') as LogonType,EXTRACT_TOKEN(strings, 9, '|') AS AuthPackage, EXTRACT_TOKEN(Strings, 11, '|') AS Workstation, EXTRACT_TOKEN(Strings, 17, '|') AS ProcessName, EXTRACT_TOKEN(Strings, 18, '|') AS SourceIP FROM 'C:\Dropbox\DFIR\Window\Behaviour\Results\Security-Export.evtx' WHERE EventID = 4624 AND Username NOT IN ('SYSTEM'; 'ANONYMOUS LOGON'; 'LOCAL SERVICE'; 'NETWORK SERVICE') AND Domain NOT IN ('NT AUTHORITY') and EXTRACT_TOKEN(Strings, 8, '|')='3' "
Failed Logon History
unsuccessful logon
C:\>LogParser.exe -stats:OFF -i:EVT "SELECT TimeGenerated AS Date, EXTRACT_TOKEN(Strings, 5, '|') as Username, EXTRACT_TOKEN(Strings, 6, '|') as Domain, EXTRACT_TOKEN(Strings, 10, '|') as LogonType,EXTRACT_TOKEN(strings, 11, '|') AS AuthPackage, EXTRACT_TOKEN(Strings, 13, '|') AS Workstation, EXTRACT_TOKEN(Strings, 19, '|') AS SourceIP FROM 'C:\temp\Security-Export.evtx' WHERE EventID = 4625 AND Username NOT IN ('SYSTEM'; 'ANONYMOUS LOGON'; 'LOCAL SERVICE'; 'NETWORK SERVICE') AND Domain NOT IN ('NT AUTHORITY')"
Find specific User
LogParser.exe -stats:OFF -i:EVT "SELECT TimeGenerated AS Date, EXTRACT_TOKEN(Strings, 5, '|') as Username, EXTRACT_TOKEN(Strings, 6, '|') as Domain, EXTRACT_TOKEN(Strings, 10, '|') as LogonType,EXTRACT_TOKEN(strings, 11, '|') AS AuthPackage, EXTRACT_TOKEN(Strings, 13, '|') AS Workstation, EXTRACT_TOKEN(Strings, 19, '|') AS SourceIP FROM 'C:\temp\Security-Export.evtx' WHERE EventID = 4625 AND Username NOT IN ('SYSTEM'; 'ANONYMOUS LOGON'; 'LOCAL SERVICE'; 'NETWORK SERVICE') AND Domain NOT IN ('NT AUTHORITY') AND Username = 'Administrator'"
Find specific IP
LogParser.exe -stats:OFF -i:EVT "SELECT TimeGenerated AS Date, EXTRACT_TOKEN(Strings, 5, '|') as Username, EXTRACT_TOKEN(Strings, 6, '|') as Domain, EXTRACT_TOKEN(Strings, 10, '|') as LogonType,EXTRACT_TOKEN(strings, 11, '|') AS AuthPackage, EXTRACT_TOKEN(Strings, 13, '|') AS Workstation, EXTRACT_TOKEN(Strings, 19, '|') AS SourceIP FROM 'C:\temp\Security-Export.evtx' WHERE EventID = 4625 AND Username NOT IN ('SYSTEM'; 'ANONYMOUS LOGON'; 'LOCAL SERVICE'; 'NETWORK SERVICE') AND Domain NOT IN ('NT AUTHORITY') AND SourceIP = '10.1.47.151'"
check ntlm based attempts
LogParser.exe -stats:OFF -i:EVT "SELECT TimeGenerated AS Date, EXTRACT_TOKEN(Strings, 5, '|') as Username, EXTRACT_TOKEN(Strings, 6, '|') as Domain, EXTRACT_TOKEN(Strings, 10, '|') as LogonType, EXTRACT_TOKEN(strings, 11, '|') AS AuthPackage, EXTRACT_TOKEN(Strings, 13, '|') AS Workstation, EXTRACT_TOKEN(Strings, 19, '|') AS SourceIP FROM 'C:\temp\Security-Export.evtx' WHERE EventID = 4625 AND Username NOT IN ('SYSTEM'; 'ANONYMOUS LOGON'; 'LOCAL SERVICE'; 'NETWORK SERVICE') AND Domain NOT IN ('NT AUTHORITY') AND AuthPackage LIKE '%NtLmSsp%' AND Username NOT LIKE '%$'"
LogOff History
C:\>LogParser.exe -stats:OFF -i:EVT "Select TimeGenerated AS Date, EXTRACT_TOKEN(Strings, 1, '|') AS Username, EXTRACT_TOKEN(Strings, 2, '|') AS Domain FROM 'C:\Dropbox\DFIR\Window\Behaviour\Results\Security-Export.evtx' WHERE EventID = 4634 AND Domain NOT IN ('NT AUTHORITY')"
'DFIR > 사용자 행위 분석' 카테고리의 다른 글
| 응용 프로그램 실행 분석-프리패치분석 (0) | 2020.03.04 |
|---|---|
| 응용 프로그램 실행 분석-MUICache (0) | 2020.03.04 |
| 응용 프로그램 실행 분석-UserAssist (0) | 2020.03.04 |
| USB 사용 이력 분석 (4) | 2020.03.03 |
| 최근 사용자 행위 (TimeLine) 분석 / Windows Activity Timeline (0) | 2020.03.03 |
최근 사용자 행위 (TimeLine) 분석 / Windows Activity Timeline
침해사고 분석 대응과 관련하여 저장장치 사용, 웹 활동 등 사용자들의 일반 행위들을 시간순으로 확인
어플리케이션 실행 , 웹 활동(인터넷 검색 등), 자주 열어본 파일 등을 시간 순으로 표시
Window + TAB 키를 치면 표시되는 데이터들이며 이 정보는 "Windows 에서 PC의 내 활동을 수집하도록 허용"
옵션을 선택 활성화해야 수집이 되며 현재를 기준으로 최대 30일 동안 사용자의 활동을 확인할 수 있습니다.
분석 내용
응용프로그램 실행 이력
인터넷 검색 등 웹 활동 이력
자주 열어본 파일이나 최근 접근 파일 확인
사용자의 과거 활동 이력 추적
사건 발생 전후 생성, 수정, 삭제, 접근한 파일 분석
파일 경로
Users\AppData\Local\ConnectedDevicesPlatform\L.\ActivitiesCache.db <- SQLite DB Format
예제
C:\Users\chohb\AppData\Local\ConnectedDevicesPlatform\c0fe10dddb98dd4b\ActivitiesCache.db
분석
Last Activity View
From : https://www.nirsoft.net/utils/computer_activity_view.html
실행중인 시스템의 다양한 소스에서 정보를 수집하고 사용자 행위 및 이벤트의 로그를 표시하는 도구
수집 데이터에는 exe 파일 실행, 열기/저장 대화 상자 열기, 탐색기 또는 기타 소프트웨어에서 파일/폴더 열기,
소프트웨어 설치, 시스템 종료/시작, 응용 프로그램 또는 시스템 충돌, 네트워크 연결/연결 끊기 등이 포함
Actions/Events List
The following actions and events are currently supported by LastActivityView:
- Run .EXE file: .EXE file run directly by the user, or by another software/service running in the background.
- Select file in open/save dialog-box: The user selected the specified filename from the standard Save/Open dialog-box of Windows.
- Open file or folder: The user opened the specified filename from Windows Explorer or from another software.
- View Folder in Explorer: The user viewed the specified folder in Windows Explorer.
- Software Installation: The specified software has been installed or updated.
- System Started: The computer has been started.
- System Shutdown: The system has been shut down, directly by the user, or by a software that initiated a reboot.
- Sleep: The computer has been placed into sleep mode.
- Resumed from sleep: The computer has been resumed from sleep mode.
- Network Connected: Network connected, after previously disconnected.
- Network Disconnected: Network has been disconnected
- Software Crash: The specified software has been crashed.
- Software stopped responding (hang): The specified software stopped responding.
- Blue Screen: Blue screen event has been occurred on the system.
- User Logon: The user logged on to the system.
- User Logoff: The user logged off from the system. This even might caused by a software that initiated a reboot.
- Restore Point Created: Restore point has been created by Windows operating system.
- Windows Installer Started
- Windows Installer Ended
- Wireless Network Connected: Windows connected to a wireless network, the connection information is displayed in the 'More Information' column.
- Wireless Network Disconnected: Windows disconnected from a wireless network, the connection information is displayed in the 'More Information' column.
GUI
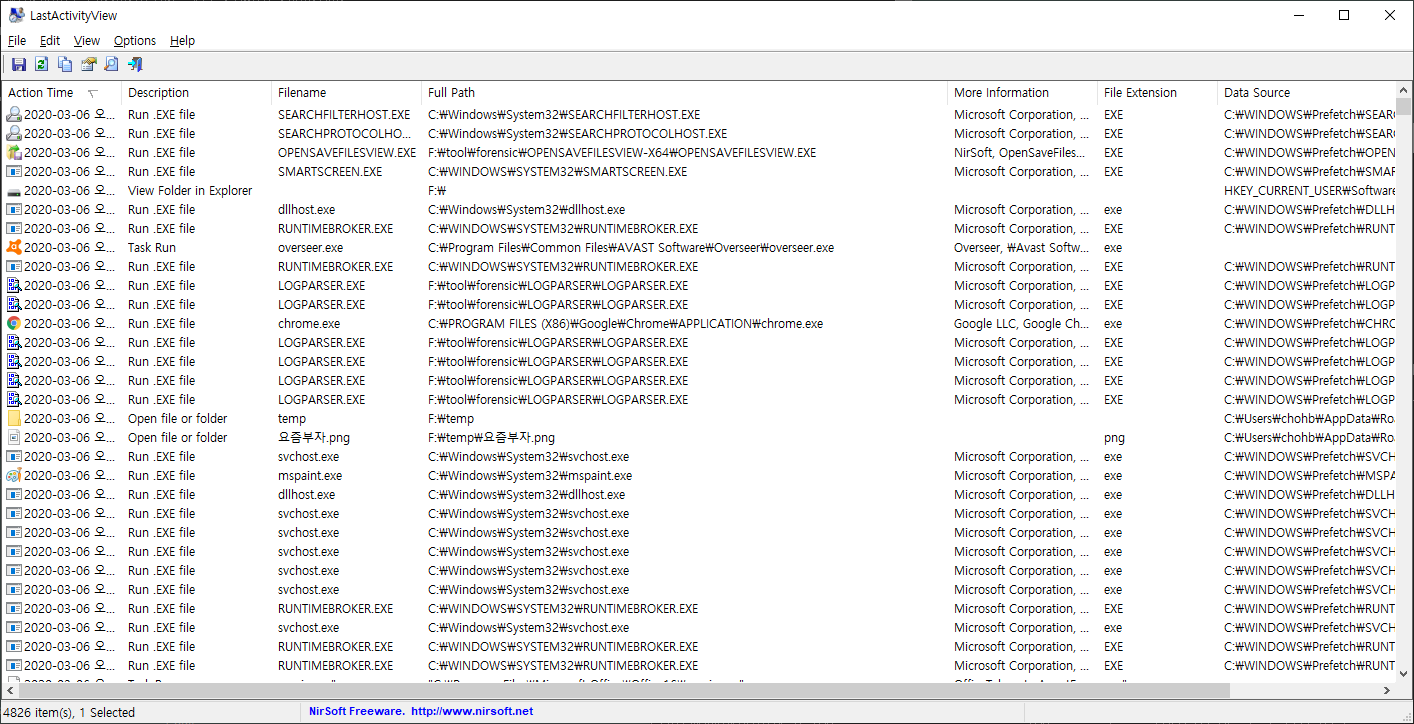
CLI
C:\>LastActivityView.exe /sort "~ action time" /sxml C:\temp\LastActivity.xml
필드명 조회
C:\>logparser.exe -h -i:xml "C:\temp\LastActivity.xml" -headerrow:on
Fields:
action_time (S) description (S) filename (S) full_path (S)
more_information (S) file_extension (S) data_source (S)
조회
C:\>logparser.exe -stats:off -i:xml "select action_time, filename, description, data_source from 'C:\temp\LastActivity.xml'"
WxTCmd
Wxtcmd는 ActivitiesCache.db 의 테이블 중 Activity테이블과 Activity_PackageIDs테이블을 파싱하여
tsv형태로 저장해준다.
F:\>WxTCmd.exe -f "C:\Users\chohb\AppData\Local\ConnectedDevicesPlatform\c0fe10dddb98dd4b\ActivitiesCache.db" --csv f:\temp\activitiescache
F:\tool\forensic\WxTCmd>dir f:\temp\activitiescache
2020-03-06 오전 10:15 1,547,408 20200306101553_Activity.tsv
2020-03-06 오전 10:15 4,452,590 20200306101553_Activity_PackageIDs.csv
F:\>LogParser.exe -h -i:tsv "f:\temp\activitiescache\20200306101553_Activity.tsv"
Fields:
Filename (S)
RowNumber (I)
Id|Executable|DisplayText|ContentInfo|StartTime|EndTime|LastModifiedTime|ExpirationTime|CreatedInCloud|LastModifiedOnClient|OriginalLastModifiedOnClient|ActivityType|IsLocalOnly|ETag|PackageIdHash|PlatformDeviceId|Duration (S)
F:\>LogParser.exe -i:tsv "select * from f:\temp\activitiescache\20200306101553_Activity.tsv"
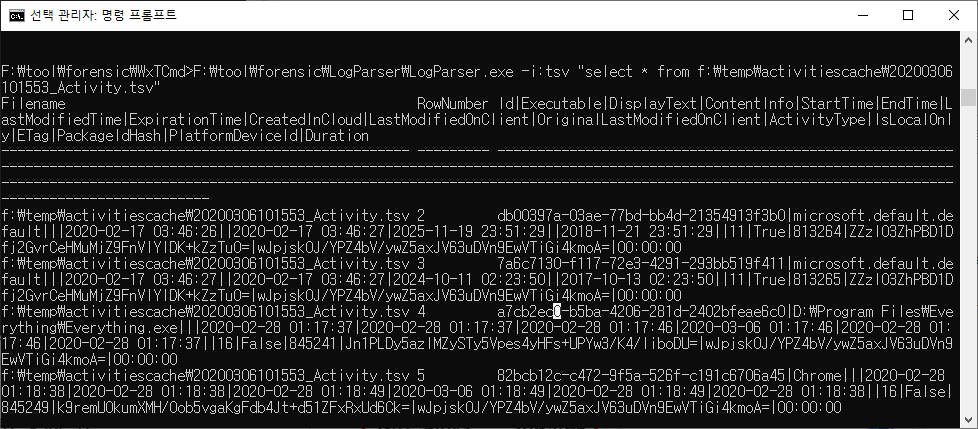
F:\>LogParser.exe -i:tsv "select * from 'F:\temp\activitiescache\20200306101553_Activity_PackageIDs.csv'"

SQLite
F:\>sqlite3.exe C:\Users\chohb\AppData\Local\ConnectedDevicesPlatform\c0fe10dddb98dd4b\ActivitiesCache.db
sqlite> .database
main: C:\Users\chohb\AppData\Local\ConnectedDevicesPlatform\c0fe10dddb98dd4b\ActivitiesCache.db
sqlite> .table
Activity Activity_PackageId DataEncryptionKeys Metadata
ActivityOperation AppSettings ManualSequence SmartLookup
sqlite> pragma table_info(Activity);
0|Id|GUID|1||1
1|AppId|TEXT|1||0
2|PackageIdHash|TEXT|0||0
3|AppActivityId|TEXT|0||0
4|ActivityType|INT|1||0
5|ActivityStatus|INT|1||0
6|ParentActivityId|GUID|0||0
7|Tag|TEXT|0||0
8|Group|TEXT|0||0
9|MatchId|TEXT|0||0
10|LastModifiedTime|DATETIME|1||0
11|ExpirationTime|DATETIME|0||0
12|Payload|BLOB|0||0
13|Priority|INT|0||0
14|IsLocalOnly|INT|0||0
15|PlatformDeviceId|TEXT|0||0
16|CreatedInCloud|DATETIME|0||0
17|StartTime|DATETIME|0||0
18|EndTime|DATETIME|0||0
19|LastModifiedOnClient|DATETIME|0||0
20|GroupAppActivityId|TEXT|0||0
21|ClipboardPayload|BLOB|0||0
22|EnterpriseId|TEXT|0||0
23|OriginalPayload|BLOB|0||0
24|OriginalLastModifiedOnClient|DATETIME|0||0
25|ETag|INT|1||0
26|UserActionState|INT|0|0|0
27|IsRead|INT|0|0|0
28|GroupItems|TEXT|0||0
29|DdsDeviceId|TEXT|0||0
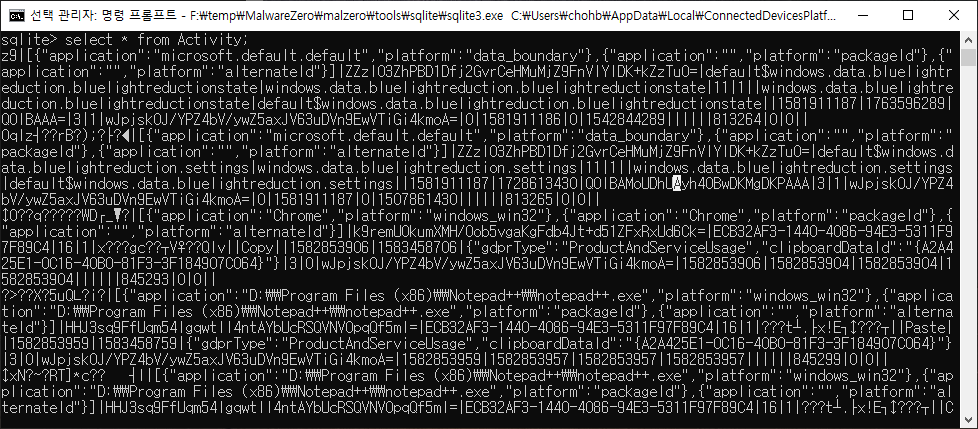
sqlite> select * from Activity;
'DFIR > 사용자 행위 분석' 카테고리의 다른 글
| 응용 프로그램 실행 분석-프리패치분석 (0) | 2020.03.04 |
|---|---|
| 응용 프로그램 실행 분석-MUICache (0) | 2020.03.04 |
| 응용 프로그램 실행 분석-UserAssist (0) | 2020.03.04 |
| USB 사용 이력 분석 (4) | 2020.03.03 |
| Log On-Off 내역 분석 (0) | 2020.03.03 |
