유용한 명령어 및 스크립트
유용한 명령어 및 스크립트
scan these directories for items of interest e.g. unusual exe, dll, bat, lnk etc files with:
dir /s /b %localappdata%\*.exe | findstr /e .exe
dir /s /b %appdata%\*.exe | findstr /e .exe
dir /s /b %localappdata%\*.dll | findstr /e .dll
dir /s /b %appdata%\*.dll | findstr /e .dll
dir /s /b %localappdata%\*.bat | findstr /e .bat
dir /s /b "%appdata%\Microsoft\Windows\Start Menu\Programs\Startup\" | findstr /e .lnk
dir /s /b "C:\Users\Public\" | findstr /e .exe
dir /s /b "C:\Users\Public\" | findstr /e .lnk
dir /s /b "C:\Users\Public\" | findstr /e .dll
dir /s /b "C:\Users\Public\" | findstr /e .bat
Scan for malware with Windows Defender
"%ProgramFiles%\Windows Defender\MpCmdRun.exe" -Scan -ScanType 1
"%ProgramFiles%\Windows Defender\MpCmdRun.exe" -Scan -ScanType 2
"%ProgramFiles%\Windows Defender\MpCmdRun.exe" -Scan -ScanType 3 -File C:\Users\[username]\AppData\Local\Temp
Check running executables for malware via VirusTotal
PS F:\temp> foreach ($process in Get-WmiObject win32_process | where {$_.ExecutablePath -notlike ""}) {Invoke-RestMethod -Method 'POST' -Uri 'https://www.virustotal.com/vtapi/v2/file/report' -Body @{ resource =(Get-FileHash $process.ExecutablePath | select Hash -ExpandProperty Hash); apikey = "바이러스토탈 API Key"}}
바이러스토탈은 원래 유료이며 무료는 분석(조회) 건수 제한이 있습니다.
List of IPV4 addresses who have connected (RDP)
Get-WinEvent -Log 'Microsoft-Windows-TerminalServices-LocalSessionManager/Operational' | select -exp Properties | where {$_.Value -like '*.*.*.*' } | sort Value -u
List Alternate Data Streams in current Dir and view them
gi * -s *
gc [FILENAME] -s [ADSNAME]
Locate BITSAdmin Persistence
bitsadmin /list /allusers /verbose
Find files without extensions
Get-ChildItem -Path C:\Users\[user]\AppData -Recurse -Exclude *.* -File -Force -ea SilentlyContinue
Obtain hash of unsigned or invalid DLLs currently loaded by processes
$A=$(foreach ($dll in gps|select -ExpandProperty modules -ea ig){Get-AuthenticodeSignature $dll.FileName |Where-Object Status -NE "Valid"|Select Path});$B=$(foreach ($dll in $A){Get-FileHash $dll.Path| select Hash -ExpandProperty Hash})|Sort-Object| Get-Unique;$B
Obtain unsigned DLL information loaded by processes
listdlls -u
Check all Appdata files for unsigned or invalid executables
Get-ChildItem -Recurse $env:APPDATA\..\*.exe -ea ig| ForEach-object {Get-AuthenticodeSignature $_ -ea ig} | Where-Object {$_.status -ine "Valid"}|Select Status,Path
Find executables and scripts in Path directories ($env:Path)
Get-Command * -Type Application | FT -AutoSize
Get-Command -Name * | FL FileVersionInfo
Find files created/written based on date date
Get-ChildItem C:\ -recurse -ea SilentlyContinue -force | where-object { $_.CreationTime.Date -match "12/25/2014"}
Get-ChildItem C:\ -recurse -ea SilentlyContinue -force | where-object { $_.LastWriteTime -match "12/25/2014"}
Get-ChildItem C:\ -recurse -ea SilentlyContinue -force | where-object { $_.CreationTime.Hour -gt 2 -and $_.CreationTime.Hour -lt 15}
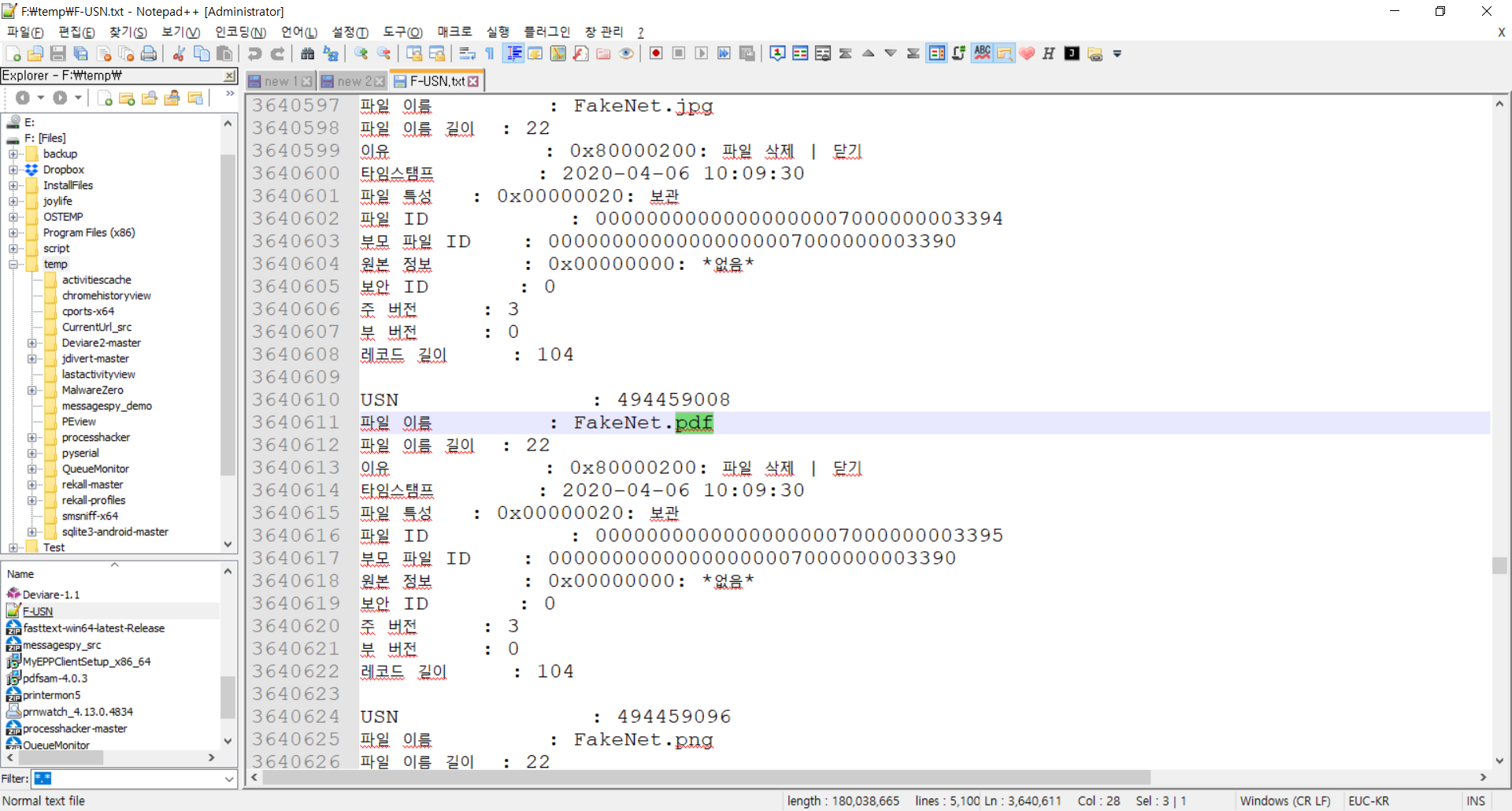
USN Journal (any changes to NTFS volume)
c:\>fsutil usn readjournal F: > f-usn.txt

'Security > Malware Analyze' 카테고리의 다른 글
| Tool - Loki, Simple IOC and Incident Response Scanner (0) | 2020.04.08 |
|---|---|
| 악성코드 분석 대상 폴더 및 레지스트리 (0) | 2020.03.12 |
